DOWNLOAD WINDOWS ANGEL LIVE V.2.0 EDITION FULL ACTIVATED

DOWNLOAD WINDOWS SMART XP V.1 FULL ACTIVATED


MAKE A PORTABLE APPLICATION WITH THINAPP

Introduction
ThinApp is an application that can be used to make some applications portable for the user. But you should make this procedure only with applications that have not already been installed on your computer.
- In this tutorial we will learn how an application with ThinApp .
- We will demonstrate with TuneUp Utilities 2009.
- ThinApp is supported Windows Seven since version 4.0.4.
How to proceed
- Step 1: Go to theStart button and select All Programs, and then chooseVMWARE before going on the “ThinApp Setup Capture” shortcut.

- Step 2: When the ThinApp Setup Capture window pops up, click on”Next”.

- Step 3: Close all the applications that can halt the process as well as the application that you want to make portable. When done, click Next.

- Step 4: The application will scan for the files required and may take some time. Do not touch anything while this process has started, it will let you know automatically when done.

- Step 5: When it has finished, minimize the ThinApp window as indicated on the screen.

- Step 6: You can now install the application that you want to make portable (for this example we have used Tune Up Utilities, available through the link:http://en.kioskea.net/download/download 1448 tuneup utilities )

- Step 7: if the application requires the serial number in order to run, enter it to validate the software. Do not forget to configure the software before proceeding to the next step.

- Step 8: When the installation is done maximize the ThinApp window and click on Next to analyse once more your system.

Compilation
- The analysis of the system will determine which folders and files are needed for the installation of the software to be able to create a portable version of it.
- Step 9: When the User-accessible entry points window pop ups, check thesoftware that need to be made portable and when this is done, you can nowclick Next

- Step 10: You can now choose the flash disk device where you want the application to run in and click Next when done.

- Step 11: Leave the Merged isolation mode checked and click Next .

- Step 12: Choose the Fast Compression option to get the maximum space that will be required on the flash disk. Click on Next.

- Step 13: The folders that will be needed by the application will hence be located in the same directory.

- Step 14: When the previous step is over, you can now click on Build Now to make a whole folder on the file contents needed to execute the portableapplication.

- Step 15: You must now choose the Browse Project option to get hold of the folder made specially for the portable software.

- Step 16: Browse for the Bin folder and double click on its icon to open it.

- Step 17: The last step left is to copy the executable application on your flash disk and you are done!
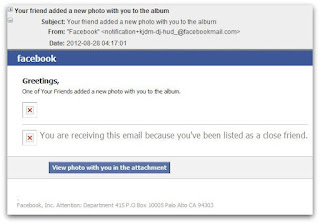
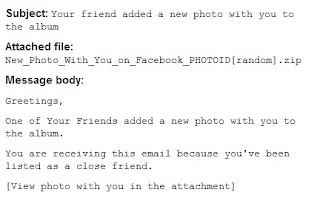
Warning : Hackers Use Facebook Photo Email Notifications for Installing Malware

How To Redirect A Website On Your Own Website

How To Redirect Defaced Website On your Website???
For Redirecting hacked website to your website open the deface Page with Notepad And paste this code Anywhere, But closed the <> Properly
Code :-
(replace devilscafe.in with your own website)
Example :-
Find this code in Your deface page and Paste the code just after This code
Example :-  Now save The Deface page and Upload on Defacedwebsite 🙂 The website will be redirect on your website !
Now save The Deface page and Upload on Defacedwebsite 🙂 The website will be redirect on your website !
See Live example of redirecting :-
http://legend-h.org/mirror/224785/fullaventura.com/jaihind.html
How To Add A Pop Up and Open Your website in a New window
If you want to Open Your website In a New Window (Pop-up) Paste this code
after
Example :-
Dont Forgot to leave a Comment if you Like this 😉
Metasploit Framework 4.4 Released

- Importing rich vulnerability data from Nexpose scans, sites, and XML
- Automatically validating the exploitability of many high-risk vulnerabilities
- Providing a simplified process to spot-check individual vulnerabilities
- Pushing granular exploit results back to Nexpose via Vulnerability Exceptions
- Pushing device classifications back to Nexpose Asset Groups via Metasploit Tags
- Enhancing Metasploit reports with detailed Nexpose scan data
- Quickly identify high-risk vulnerabilities not protected by compensating controls
- Measure the effectiveness of defensive solutions designed to mitigate vulnerabilities
- Increase credibility and reduce friction between IT operations and security teams