Shodan – The Worst Internet Search Engine
How to Turn Off Beeping Sound Notifications in Facebook
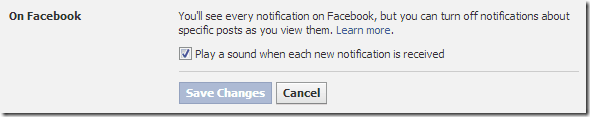
Facebook has recently additional another smart beeping feature for notifying user World Health Organization isn’t really viewing the Facebook screen, therefore if you’re exploitation another web site at constant time exploitation facebook and if anyone likes or comments or do any quite activity you’re planning to get a beep sound that may apprise you that somebody has done one thing on facebook.
So currently if you think that that feature isn’t smart and you only got to get eliminate that beep sound well currently you’ll be able to by following below straightforward steps.
- Visit Facebook.com
- Click on the tiny gear icon on prime right.
- Now simply opt for Account Settings.
- Now you may be taken to the account settings page, simply opt for Notifications Head.
- Now underneath On Facebook choice you would like to UN certify sound beep notification choice.
6. Now click on Save Changes button and revel in, currently no sound would ever disturb you on Facebook, currently anytime you would like to urge it enabled simply check that choice 🙂
Get 2000 Twitter Followers Free Within a Day
Requirments
- A Twitter ID ( LOL! what I Mention this!)
- Its ought to be 6 months previous
- it ought to have 100+ tweets
- it ought to have 100+ followers
Steps
- Go To SEOclerk and make and account there.
- then visit The Link
- Then follow steps there
- tweet the tweet provided there
- follow @seoclerks
- then enter your twitter username in on top of box and click on verify
- Now you will get 2$ take advantage your balance
- Now visit This Link and click on Order
- Now At Payment choice choose pay victimization my balance
- now you will be asked for you twitter username on next page
- just enter your twitter username like @OrtohinAsad
Password Protection for Google Chrome Bookmarks
Hack your Windows Experience Index
Step
- Go to C:\Windows\Performance\WinSAT\DataStore and find (yyyy-mm-dd hh.mm.ss.ms Formal.Assessment (Recent).WinSAT.xml) then open with notepad.
- Second, change scores to #.# (Max: 7.9) then Save.
Lastly, view your system properties.
View Private Facebook Profile Pictures in Original Size
https://www.facebook.com/bananaphone2005
Here is Zoey, not that famous, but in a few shows.
She has a pictures set on private, and I am curious to what’s in her profile picture. Copy the link on your picture first…
Here it is.
Now go to YOUR profile picture, click it into bigger view, and copy THAT link.
https://sphotos-b.xx.fbcdn.net/hphotos-p…*_**_n.jpg
As you can see they are two different links.
Take your link, once again
https://sphotos-b.xx.fbcdn.net/hphotos-p…*_**_n.jpg
And take the celeb’s links NUMBERS which are; 541792_393338197421815_97339562 and put them where I starred them.
541792_393338197421815_97339562
https://sphotos-b.xx.fbcdn.net/hphotos-prn1/541792_393338197421815_97339562_n.jpg