Microsoft release Attack Surface Analyzer tool released
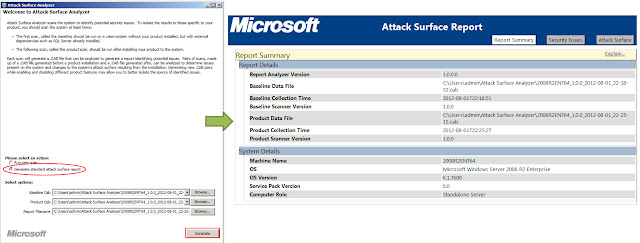
- Developers to view changes in the attack surface resulting from the introduction of their code on to the Windows platform
- IT Professionals to assess the aggregate attack surface change by the installation of an organization’s line of business applications
- IT Security Auditors to evaluate the risk of a particular piece of software installed on the Windows platform during threat risk reviews
- IT Security Incident Responders to gain a better understanding of the state of a systems security during investigations (if a baseline scan was taken of the system during the deployment phase)
Backtrack 5 R3 Released
Download BackTrack 5 R3 release via torrent
BT5R3-GNOME-64.torrent (md5: 8cd98b693ce542b671edecaed48ab06d)
BT5R3-GNOME-32.torrent (md5: aafff8ff5b71fdb6fccdded49a6541a0)
BT5R3-KDE-64.torrent (md5: 981b897b7fdf34fb1431ba84fe93249f)
BT5R3-KDE-32.torrent (md5: d324687fb891e695089745d461268576)
BT5R3-GNOME-32-VM.torrent (md5: bca6d3862c661b615a374d7ef61252c5)
NinjaWPass – Protect WordPress against keyloggers and stolen passwords
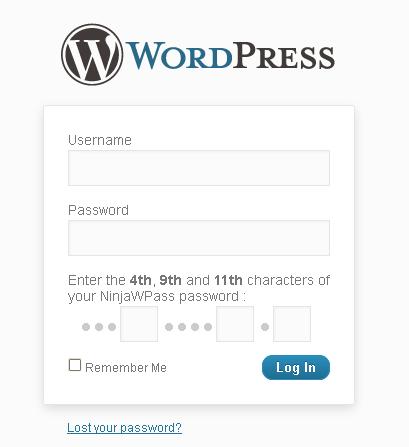
At the WordPress login prompt, besides your current password, you will be asked to enter 3 randomly chosen characters from your NinjaWPass password. Whether your computer is infected by a keylogger or someone is spying over your shoulder, this protection will keep them away.
Additionally, the plugin offers the possibility to receive an alert by email whenever someone logs into your WordPress admin interface
HTExploit : Open Source Tool to Bypass Standard Directory Protection
- Multiples modules to execute.
- Save the output to an specify directory.
- HTML Reporting.
- Use multiples wordlist to probe against htaccess bypassing.
- Mode verbose for a full detailed information.
- Multi-platform and flexible.
WebSploit Toolkit v.1.9 – Tcp Kill Attack Added
- Autopwn – Used From Metasploit For Scan and Exploit Target Service
- wmap – Scan,Crawler Target Used From Metasploit wmap plugin
- format infector – inject reverse & bind payload into file format
- phpmyadmin – Search Target phpmyadmin login page
- lfi – Scan,Bypass local file inclusion Vulnerability & can be bypass some WAF
- apache users – search server username directory (if use from apache webserver)
- Dir Bruter – brute target directory with wordlist
- admin finder – search admin & login page of target
- MLITM Attack – Man Left In The Middle, XSS Phishing Attacks
- MITM – Man In The Middle Attack
- Java Applet Attack – Java Signed Applet Attack
- MFOD Attack Vector – Middle Finger Of Doom Attack Vector
- USB Infection Attack – Create Executable Backdoor For Infect USB For Windows


